You might also like: aNmap – Android App For Hackers
Today I’m going to give you a step by step guide on how to use zANTI.
Before jumping into the how-to guide, take a look at some of the things you can do with zANTI:
- Change device’s MAC address.
- Create a malicious WiFi hotspot.
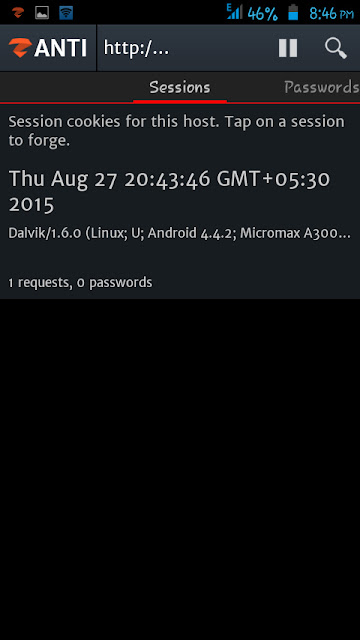
- Hijack HTTP sessions.
- Capture downloads.
- Modify HTTP requests and responses.
- Exploit routers.
- Audit passwords.
- Check a device for shellshock and SSL poodle vulnerability.
Note: Before installing the app, make sure your device is rooted properly and you have installed SuperSU on the device.
You might also like: FaceNiff Tool – Android App For Hackers
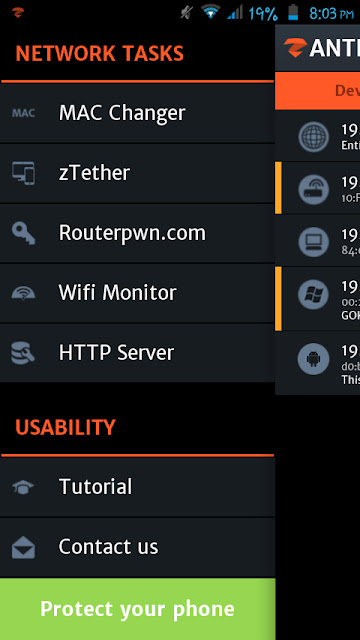
How To Use zANTI:
6. Tap on “Finish”. You will see a screen as shown below:
Mac Changer
How To Use Mac Changer:
zTether
How To Use zTether:
Moving onto the next program module….
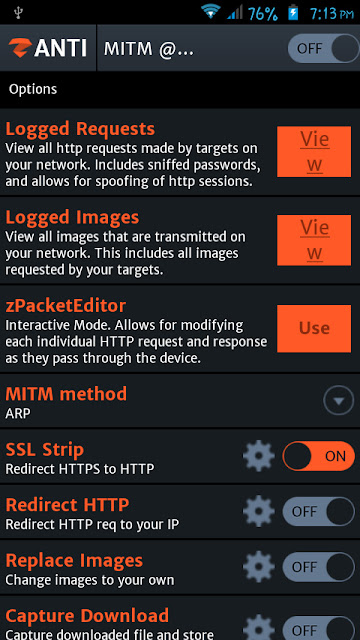
zPacketEditor
It allows you to modify HTTP requests and responses on your network. It is basically an interactive mode that can allow you to edit and send each request and response.
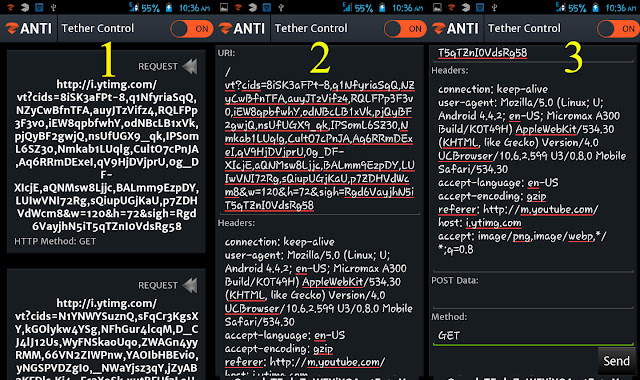
How To Use zPacketEditor:
First, tap on “zPacketEditor” and then turn on the module. You will see the live requests and responses there (1). If you want to edit a particular request or response, swipe it to the right (2). After the edit, you can tap on “Send” button (3).
You might also like: DroidSheep – Android App Download
Moving onto the next functionality….
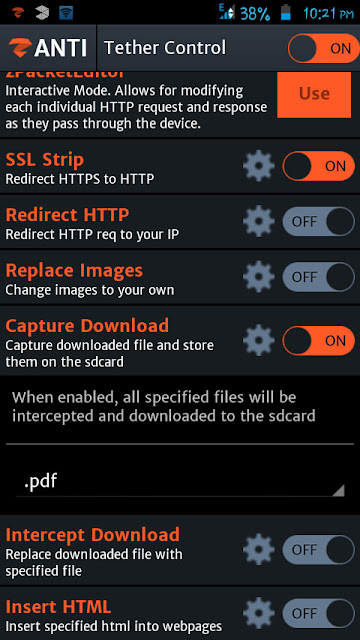
SSL Strip
SSL Strip is a type of Man In the Middle Attack that forces victim’s browser into using HTTP instead of HTTPS (SSL Strip is turned on by default).
Note: Websites using HSTS (HTTP Strict Transport Security) are immune to SSL Strip attacks.
Moving onto the next one……
Redirect HTTP
It allows you to redirect all HTTP traffic to a site or server. For example, If you turn on the “Redirect HTTP”, it will redirect all HTTP traffic to Zimperium servers (default configuration). But if you want to forward all the traffic to a particular site, tap on the settings icon, you will see an area to enter a URL (see the image below). Enter a URL in the field and then again tap on the settings icon.
Now moving onto my favorite MITM module….
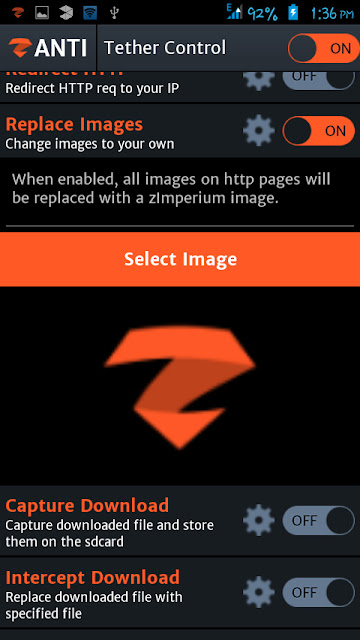
Replace Images
Now, the users will see the selected image everywhere on the web!
Moving onto the next one…..
Capture Download
It allows you to intercept and download all specified files to the SD card. For example, if you want to capture pdf files, you have to tap on the settings icon and then select the .pdf from the menu. Then turn on “Capture Download”.
Intercept Download
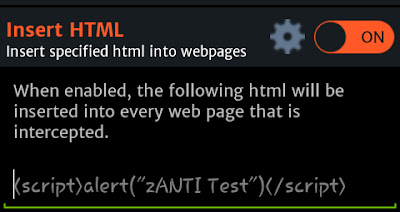
Insert HTML
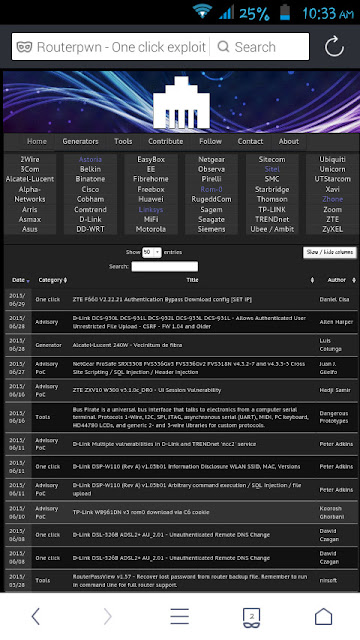
Routerpwn.com
How To Use Routerpwn.com:
WiFi Monitor
HTTP Server
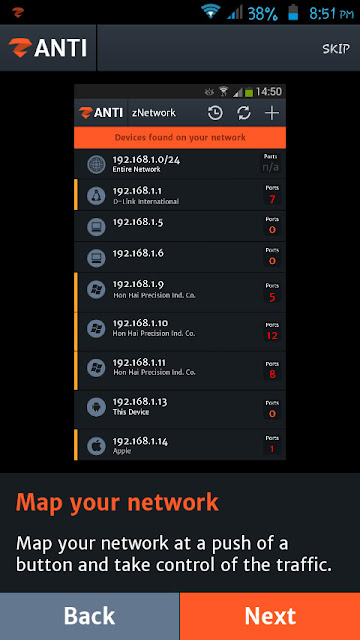
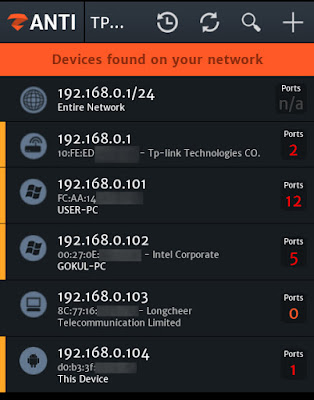
How To Scan a Target Device?
How to Establish Connection to a Device?
Password Complexity Audit
Note: You cannot change the cracking method on the free version of zANTI.
Turn off the “Automatic Mode” to audit a particular protocol. In the Automatic Mode, you should tap on the “Go” button to start the audit.
How To Perform MITM Attack?
MITM Method
- From the view of the Router – Attackers machine is the user’s machine.
- From the view of victim’s computer – Attackers machine is the router.
How To Check a Target For “ShellShock” Vulnerability?
First, select the target device. Then tap on “ShellShock”. It will start scanning the target (see the image below):
Wait for some time. After scanning the target device, it will display the result.