Financial institutions have yet another money security headache on their palms, because Automated Teller Machines are being infected by malware which is becoming increasingly sophisticated in its aim to let criminals blatantly empty out money spitting machines installed on the corners of roads, shops, etc., without needing to have beforehand sourced the credit or debit cards of legitimate people, and getting away with sneaky techniques without being detected.
To begin with, the ATM is required to be taken over with the GreenDispenser malware. For this, the attacker needs to be physically present at the ATM, or some help from banking employees. But once the malware is established in the Automatic Teller Machine, a message will appear that will say that the machine is out of service why the message so that no one can use the machine to withdraw cash and the attacker can have all for himself.
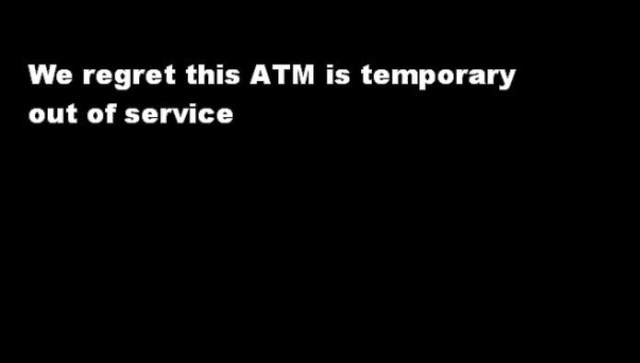
Next, the attacker needs to enter a fixed authorization PIN code that will grant them special access to the system. Remarkably, in order to avoid other hackers from abusing the PIN number, the malware includes a two-way authentication feature to verify that the person typing the PIN code is who they are saying to be. That’s a better security protection than nearly any legitimate financial institution that they provide to customer every time they utilize an ATM. However, there is more, together with the initial hardcoded PIN registered, the ATM burglar is presented with a QR code, that is scannable with many applications in the iOS and Android market. Once the QR code is scanned it produces a second PIN, which will open up the ATM menu, disclosing all the options to eliminate or even securely erase the malware out from the ATM in a bid in order to prevent evaluation by security professionals.

Malware spreading in the ATMs is, regrettably, nothing exciting there are hundreds of articles that have mentioned numerous times in the past on groups of hackers that have swiped vast amounts of money after setting up a virus that enables them to pull out card information on ATM customers or even empty out the machines that are next to the bank themselves. The experts at Symantec point out that GreenDispenser is thought to have been found in specific regional locations like Mexico. The experts fear that if this virus becomes successful – which it has proven to be by so far – its new versions could soon be available internationally for hackers to take control of the ATM’. And it surely does not come as a surprise that this malware would be available on the darknet with a hefty price tag attached to it. It is always a good idea not to go to ATM’s that you are not familiar with – or one should at least be up to date with the bank employees and report if they see something strange.
However, current ATMs have enhanced safety measures, like encoded hard-drives, which can prevent these types of installation tactics. However, for an older ATMs still operating on Windows XP, securing against these types of assaults is far more challenging, particularly when the ATMs are deployed in various remote locations. Another problem that needs to be addressed is the physical protection of the computer system situated inside the ATMs covering. While the ATM’s money is secured inside a safe, computers commonly are not. Without sufficient actual protection for those old ATMs, the hacker has the advantage. But a wide range of actions can be taken to make things more difficult for the criminals. The financial institutions can upgrade their computer systems to Windows, 7, 8 or even 10. Install proper physical shielding as well as installing properly protected the security or CCTV cameras that can monitor the ATM all the time. Further, they can always password protect the BIOS and disable any other USB slots except the one(s) being used. Almost every system now has default disk encryption so the banks can use them and buy something much more advanced. Security service providers such as Kaspersky, ESET and others are offering custom build protection software developed for ATMs, they can be used as well. If all these guidelines are followed it will become much harder for the hackers to compromise – except if the attacker is the bank employee themselves.